
THREAT FACTOR | EPISODE 6
IT's Surprise
Security Struggle
When an IT Director's worst nightmare happens, how do he and his team work to decipher the issue?

LIKES:
Technology advancements, strategic planning, problem-solving
DISLIKES:
System downtime, budget constraints, inadequate resources
JOB RESPONSIBILITIES:
• Develop and implement IT
policies and best practices
• Help the IT department resolve
internal employee IT issues
• Communicate the company’s
security status with executives
• Respond to and investigate
cybersecurity incidents
An Onslaught of Priorities
I’d like to be entirely candid with you. I know the cloud migration project has monopolized a significant portion of your time, and it’s quite a hefty endeavor. But it’s admittedly spread me a bit thin and has left me unable to manage the operational side of the IT team efficiently. Between coordinating daily responsibilities and pushing forward our security initiatives—like the recent security awareness training—it’s been quite the balancing act. I’ve been consistently working late nights to keep things moving and, as a result, have missed my martial arts class twice this month. I’ll admit, in my haste to manage everything, I’ve had to cut a few more corners than I’m typically accustomed to. It’s not something I’m proud of, but it’s been a necessity with everything going on.
As you know, one of the critical tasks I’m overseeing is the implementation of multi-factor authentication across all employee devices, including those in our brick-and-mortar locations. The team assured me that we would be able to complete the project early last week, but due to some technical glitches, we had to delay the rollout by a couple of weeks. It’s no worries, though. It would be imprudent of me to blame our team.
First Signs of Trouble
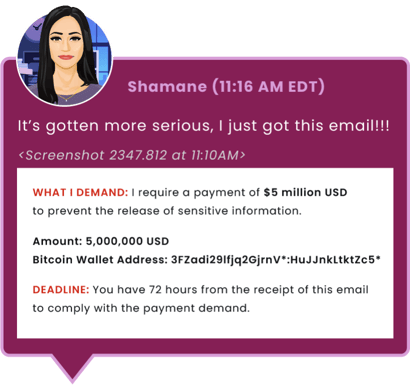
Things undoubtedly began to plummet when Shamane informed me about the ransom. I remember the exact moment—my mind instantly started mapping out potential breach points, considering every possible scenario. I knew it was a situation that demanded swift and decisive action. Initially, Shamane and I suspected a business email compromise, given that she had shared her login credentials with Wes over email the day prior. It seemed like a plausible entry point for an attacker, so I tasked one of our team members to investigate this angle thoroughly.
Meanwhile, I divided the rest of the team. Half were dedicated to diagnosing the nature of the breach, while the other half focused on managing the immediate repercussions—namely, keeping our stores operational during the breach. And I struggle to admit this, but quickly after delegating tasks to the team, it became painfully apparent that they lacked the necessary cybersecurity expertise. The team has always been more geared towards system maintenance and support, not crisis management. At that moment, I had a stark realization that their current skills were inadequate for a situation of this caliber.
Combing for Clarity
By the next day, our progress was frustratingly slow. Despite working around the clock, we hadn’t made much headway in identifying the source of the breach. The team was tired, and morale was low, but I pushed them to keep going. I knew we couldn’t afford to let this drag on—our customers’ trust was at stake, not to mention our reputation.
In the midst of it all, I got a call from Chris, our Marketing Director. He couldn’t log back into his Shopify account, and since we’ve been friends for years, I figured I’d help him out myself. It was a welcome distraction, if only for a moment. I got him back in quickly, but an hour later, he called again, saying he had misplaced the password I had just given him and needed it again. That second call struck me as odd—Chris isn’t usually that forgetful. But I was too focused on the breach to think much of it. I gave him the info and moved on, needing to get back to the task at hand.

