
PROLOGUE
Here's How it
All Began...
This story is inspired by true events. One morning, store associates at the 23 remaining Shutter Pro brick-and-mortar locations arrived at work, booted up their POS systems, and were met with a chilling surprise. A mysterious note appeared on their screens, announcing that their company was being held for a $5 million ransom.
Shocked and unsure of what to do, they quickly escalated the issue to the internal IT department. The immediate directive was to only accept cash transactions and record them by hand while the IT team scrambled to investigate the issue.
As the day progressed, the situation worsened. The CEO received an ominous email, echoing the ransom demand and threatening to distribute customer credit card data and personal information if the ransom wasn’t paid.
It has now been a week since that fateful morning. The entire team remains on high alert, working tirelessly to resolve the crisis. The CTO, who is currently in the midst of Shutter Pro’s big cloud migration, has taken on the critical task of interviewing key employees to uncover the root of the breach and find a way to secure their company’s future.
THREAT FACTOR | EPISODE 1
Quite Possibly the Worst Day of My Life
I’m here to take you through it all, from the moment I sensed trouble brewing in our policy discussions to the frantic days that followed.
LIKES:
Photography, creativity, innovation, strategic risk-taking, networking
DISLIKES:
Micromanagement, bureaucracy, inefficiency, mundane business practices
JOB RESPONSIBILITIES:
• Creative vision for the company’s
future
• Attends events to network with
potential partners
• Strategic goal setting for all teams
• Maintain overall company morale
• Main point of communication
between the investors and
operators
How One Decision Dominoed Into a Disaster
I walked into the office that day feeling happy and hopeful. I had just watched the jaw-dropping finale of “The Mole” on Netflix the night before while eating the delicious ayam bakar my husband made me. It was such a wonderful night! As soon as I got in, Wes, our amazing and helpful Chief of Staff, reminded me about our weekly executive board meeting and quickly walked me through the agenda before everyone came into the conference room. For some reason, it felt particularly intense that day. I contemplated getting a quick walk in before our meeting to lift my mood, but sadly ended up not having enough time.
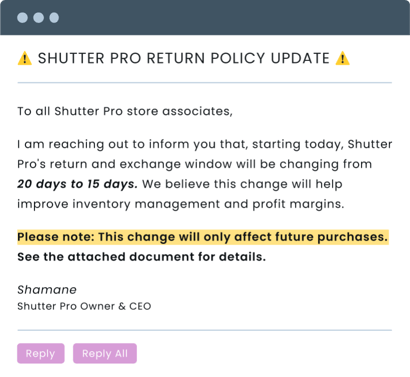
After you gave that great update about our cloud migration, we moved on to the next item and discussed how our lenient return and exchange policy was bleeding us dry. As you may remember, I was reluctant but agreed to reduce the return period from 20 to 15 days.
I was worried about customer backlash but was assured that the legal team deemed it necessary to recoup lost revenue. Later that afternoon, I drafted a company-wide email outlining the policy change, ran it by legal, and sent it to all our store managers. In the email, I made sure to emphasize that the change would only apply to new purchases.
The next day, I remembered I had missed the latest security training issued by your team. I asked Wes to block some time on my calendar to take it at a later date. That’s when he told me shared calendar access wasn’t working for him. Frustrated, I tried logging in to fix it, only to realize I had forgotten my password. In a moment of sheer absent-mindedness, I reset my login credentials and emailed them to Wes so he could update them on his device before hopping into my next meeting.
Was This All My Fault?
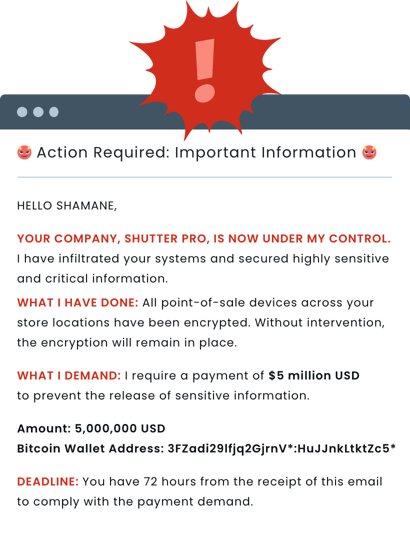
That following morning, all the blood drained from my face as I opened the email demanding a $5 million ransom. The sender claimed to have customer credit card data and personal information, threatening to distribute them if I didn’t pay the ransom.
My heart sank as my mind immediately went to my carelessness with the login credentials the day before. How could I have been so reckless? Did I open the door for this breach? Panic and guilt started to set in as I reached out to our IT Director, Ed, to discuss how my email might have been compromised and how we could mitigate further damage.
The next couple of days were honestly a blur. I was in crisis meeting after crisis meeting and spent most of those 48 hours troubleshooting with your team. We were in full damage control mode, trying to understand the extent of the breach and how to contain it. Desperately, I even asked ChatGPT what I should do in this situation. There were so many times I thought to myself: Should I just pay the ransom and eat the cost?
Each time, however, I thought back to the initial conversation I had with our attorney after the breach. He read an article on the FBI’s stance against paying ransoms, which said they strongly advised against it. The article emphasized that it could encourage more attacks and doesn’t guarantee that the stolen data will be returned.
I realized that giving in might make us more vulnerable. Plus, there was no proof that the attacker actually had the photos or credit card information they claimed. How was that even possible? How could they have obtained those? I was skeptical about the attacker and was confident that your team could restore everything from our backups. Ultimately, it was risky not to pay the ransom, but I’m confident it was the best choice for our company’s long-term security and integrity.
